
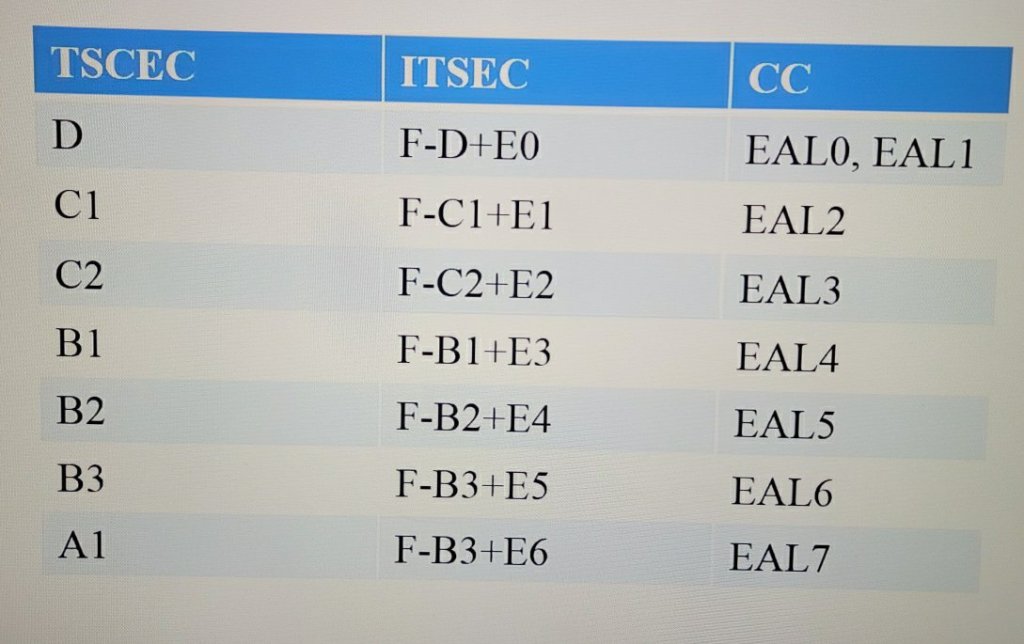
How do we evaluate security? One way is the Orange Book. This is the trusted computer system evaluating criteria. It is used by the department of defense to protect systems and networks given a security level making it suitable to protect the confidentiality of information.
This was based on the Bell-LaPadula model. Decision makers would use this model to evaluate the security level of risk a system would be rated.
The model begins with Division C1: Discretionary Security Protection. This requires identification and authentication protection. The system must enforce access and identify system faults.
Divison C2: Controlled Access Protection is a higher level of protection including C1 protection in addition to having the capability to audit and monitor individuals on a system.
Divison B1: Labeled Security means the system requires higher level of security. The security model must be addressed and the system must be labeled.
Divison B2: Structured Protection means you now have to specifically manage covert channels. Privileges must be separated as well.
Divison B3: Security Domains is the highest level of security requiring specific intrusion detection capabilities and recovery procedures for the system.
Divison A1: Verified Design is a complete independent review of the system to ensure the controls have been implemented.
Information Technology Security Evaluation Criteria (ITSEC) model was created for testing systems and products for the public to use. They are rated based on what form of testing was completed to give a level of assurance of what has been tested by common criteria:
- EAL 1 – Functionally tested
- EAL 2 – Structurally tested
- EAL 3 – Methodically tested/checked
- EAL 4 – Methodically designed
- EAL 5 – Semi formally designed
- EAL 6 – Semi formally verified
- EAL 7 – Formally verified
Three things to review from the common criteria report is the Protection Profile (PP) which includes organizational security requirements of the system. The Security Target (ST) which is the functionality and claims made by the vendor. The the Target of Evaluation (TOE) which is the assessment criteria based on the match between the security target and protection profile. The table below shows the relationship between these evaluation methods.
Two ways to evaluate a system is certification or accreditation. Certification is the verification if security is appropriate for an organization’s needs. Accreditation is the formal acceptance by management of the security level provided and the level of risk associated to its usage.